Samples of Scott Solutions Projects
Below you'll find a sample of some of the projects we have completed for our customers. You can be confident that we can perform these same projects for you, or let us sit down with you and devise a solution that fits your current need. Contact us to get more details or to set up an appointment.
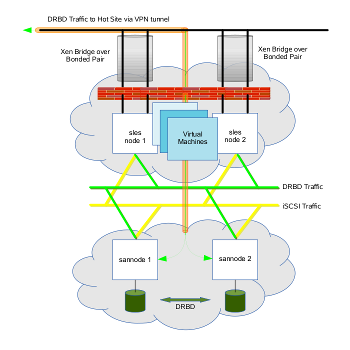
One of our projects was to build a High Availability Cluster for Virtual Machines. The image to the left depicts a robust environment whereby the VM's are distributed across two hosts that communicate with one another. They share connections to a separate cluster that contains hosts acting as a real-time “disk-to-disk” network mirror, and behaves like a SAN to the out-facing cluster. The features of this solution are as follows:
- The cluster is configured so that if one server fails, the other assumes the responsibility of running the functions originally established on the previous. This configuration maximizes the availability of services to the end user community.
- Off-server storage is established in a Storage Area Network (SAN) to ensure high availability of the content. The SAN is resident on a private network, accessible only to the nodes (servers) in the cluster. This keeps the content of the SAN secure from unauthorized access, while maximizing availability to authenticated users.
- The primary function of the cluster is to host virtual machines (VMs) in a “cloud-like” manner that provide the various services to the end user community. Virtual machines offer advantages over their physical counterparts in that VMs are more portable, can be established more readily, and provide for quicker recovery from disasters. It is more efficient to bring a VM on-line than it is to procure hardware and build a physical server in the same environment.
- Any virtual machines that are deployed in an Operations Center can be targeted for off-site replication at a designated Hot Site for disaster recovery purposes. The network mirror is modular, and can be configured to replicate content to a remote location, thus providing near real-time, up-to-date information at a location where VMs can be “spun” up at a moment's notice following a disaster.
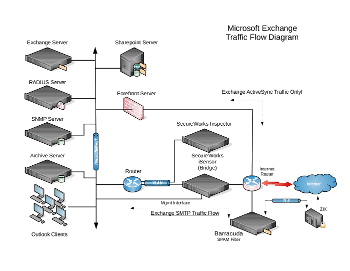
Corporate E-mail Deployment
- Microsoft® Exchange Server
The Customer will use Microsoft Exchange running on a Microsoft Windows Server platform. End-users will use Microsoft Outlook to communicate with it and read their e-mail. - Microsoft® Forefront Threat Management Gateway
The Customer will deploy Microsoft Forefront running on a Microsoft Windows Server platform. Microsoft SQL Server will be the database engine being used to manage the firewall database. The primary purpose of this system will be to act as a firewall to manage inbound traffic for Microsoft Exchange ActiveSync. The Customer will use EAS to synchronize Exchange e-mail with mobile devices.
- GFI® Mail Archive Server
The Customer will implement an e-mail archive solution provided by GFI. It runs on a Microsoft Windows Server platform, using Microsoft SQL Server for its database engine. The Archive server is responsible to capturing e-mail content from the Microsoft Exchange server and archiving it for long term research and retrieval. - Microsoft® Sharepoint Server
The Customer will use Microsoft Sharepoint as an internal repository (Intranet) for documentation and other resources. The Microsoft Exchange server will be configured to deliver content to the Sharepoint server as it is received. - Barracuda® SPAM Filter
The Customer will utilize a Barracuda SPAM filtering Internet appliance as its Internet facing SMTP gateway. All inbound and outbound SMTP traffic will pass through it. The function of the Barracuda appliance is to inspect e-mail content for SPAM and viruses, and either to block it or pass it through, based upon rules that are configured within the appliance. As an added security feature, all outbound e-mail can be relayed via TLS to a third party like Zix Corporation, that can further inspect content for non-public, personally identifiable information (NPPII).
There will be additional components in the proposed network path of the e-mail traffic, such as routers and switches, which have unique configurations. The “House” network will use a router that has been configured with a dedicated VLAN, and consumes two physical ports that connect to two appliances managed by a monitoring company, such as SecureWorks, which inspect network traffic for malicious activity. From there, the network traffic will pass through an Internet facing router, which sends it to various other subnets that connect to the components mentioned above, and eventually out to the Internet.
This proposal references several third party vendors that offer services which address specific needs outlined in it. Similar designs can be proposed with other providers; it's a matter of finding the right partners with the right features to meet the customer's needs.
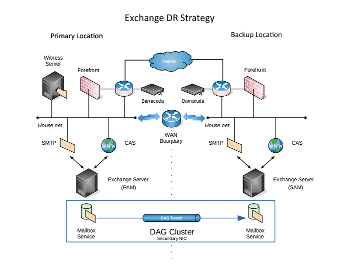
Microsoft Exchange Mailbox Off-Site Replication
A lot of our projects include Disaster Recovery features built into them. In this scenario, a customer wished to have a fully redundant corporate e-mail solution with off-site recoverability. The strategy included the introduction of a second Microsoft Exchange server that is part of the same domain. As can be seen from the diagram, many of the functions installed are identical to those presented in the previous scenario. The significant feature of this solution is the establishment of a Database Availability Group (DAG) that spans two Local Area Networks (LAN's).
From the diagram, you can see that the mailbox service at the primary location is linked to the mailbox service at the backup location through a DAG tunnel – a secured communications connection using SSL/TLS, similar to a VPN. Compression is also in place to maximize content transfer across a slower link. This can be accomplished over existing network devices (NIC's), but the process significantly hampers communications with Outlook clients.
Microsoft recommends performing this function over a dedicated NIC with unique IP addresses, although it is possible to team existing NIC's and increase overall bandwidth, thus reducing response times to Outlook clients while streaming mailbox data at the same time.
The DAG Cluster is possible with the introduction of Windows Clustering Services, which allows us to synchronize content from one Mailbox Server to another, and fail over to the remote site in the event of a disaster, either automatically or under controlled conditions. A “Witness” server is used to keep the ownership of the cluster honest. In this way, there is a tie breaker in the voting process as to which machine owns the primary functions of the cluster. In this scenario, the customer elected to implement a manual fail-over configuration. This provided them an extra level of assurance that the cluster would not fail over during times when minor WAN outages are experienced.
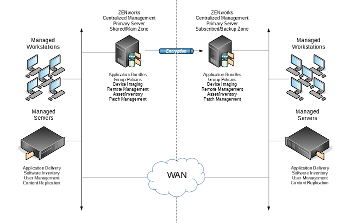
Centralized Desktop Management